Thank goodness for computer networks! If they'd never been invented, you wouldn't be reading this now (using the Internet) and I wouldn't be writing it either (using a wireless home network to link up my computer equipment). There's no doubt that computer networking is extremely complex when you delve into it deeply, but the basic concept of linking up computers so they can talk to one another is pretty simple. Let's take a closer look at how it works!
What is a computer network?

Photo: Testing a small computer network linked to the Internet. Photo courtesy of NASA Glenn Research Center (NASA-GRC).
You can do lots of things with a computer but, connect it up to other computers and peripherals (the general name given to add-on bits of computer equipment such as modems, inkjet and laser printers, and scanners) and you can do an awful lot more. A computer network is simply a collection of computer equipment that's connected with wires, optical fibers, or wireless links so the various separate devices (known as nodes) can "talk" to one another and swap data (computerized information).
Types of networks
Not all computer networks are the same. The network I'm using to link this laptop to my wireless router, printer, and other equipment is the smallest imaginable. It's an example of what's sometimes called a PAN (personal area network)—essentially a convenient, one-person network. If you work in an office, you probably use a LAN (local area network), which is typically a few separate computers linked to one or two printers, a scanner, and maybe a single, shared connection to the Internet. Networks can be much bigger than this. At the opposite end of the scale, we talk about MANs (metropolitan area networks), which cover a whole town or city, and WANs (wide area networks), which can cover any geographical area. The Internet is a WAN that covers the entire world but, in practice, it's a network of networks as well as individual computers: many of the machines linked to the Net connect up through LANs operated by schools and businesses.
Rules
Computers are all about logic—and logic is all about following rules. Computer networks are a bit like the army: everything in a network has to be arranged with almost military precision and it has to behave according to very clearly defined rules. In a LAN, for example, you can't connect things together any old how: all the nodes (computers and other devices) in the network have to be connected in an orderly pattern known as the network topology. You can connect nodes in a simple line (also called a daisy chain or bus), with each connected to the next in line. You can connect them in a star shape with the various machines radiating out from a central controller known as the network server. Or you can link them into a loop (generally known as a ring). All the devices on a network also have to follow clearly defined rules (called protocols) when they communicate to ensure they understand one another—for example, so they don't all try to send messages at exactly the same time, which causes confusion.
Permissions and security
Just because a machine is on a network, it doesn't automatically follow that every other machine and device has access to it (or can be accessed by it). The Internet is an obvious example. If you're online, you get access to billions of Web pages, which are simply files stored on other machines (servers) dotted all over the network. But you can't access every single file on every single computer hooked up to the Internet: you can't read my personal files and I can't read yours, unless we specifically choose for that to happen.
Permissions and security are central to the idea of networking: you can access files and share resources only if someone gives you permission to do so. Most personal computers that connect to the Internet allow outgoing connections (so you can, theoretically, link to any other computer), but block most incoming connections or prohibit them completely. Servers (the machines on the Internet that hold and serve up Web pages and other files) operate a more relaxed policy to incoming connections. You've probably heard of hacking, which, in one sense of the word, means gaining unauthorized access to a computer network by cracking passwords or defeating other security checks. To make a network more secure, you can add a firewall (either a physical device or a piece of software running on your machine, or both) at the point where your network joints onto another network or the Internet to monitor and prohibit any unauthorized, incoming access attempts.
What makes a network?
To make a network, you need nodes and connections (sometimes called links) between them. Linking up the nodes means making some sort of a temporary or permanent connection between them. In the last decade or so, wireless connections have become one of the most popular ways of doing this, especially in homes. In offices, wired connections are still more commonplace—not least because they are generally faster and more secure and because many newer offices have network cabling already in place.

Photo: If your laptop doesn't have a network card, you can simply plug in a PCMCIA adapter like this one. The adapter has a network card built into it.
Apart from computers, peripherals, and the connections between them, what else do you need? Each node on a network needs a special circuit known as a network card (or, more formally, a network interface card or NIC) to tell it how to interact with the network. Most new computers have network cards built in as standard. If you have an older computer or laptop, you may have to fit a separate plug-in circuit board (or, in a laptop, add a PCMCIA card) to make your machine talk to a network. Each network card has its own separate numeric identifier, known as a MAC (media access control) code or LAN MAC address. A MAC code is a bit like a phone number: any machine on the network can communicate with another one by sending a message quoting its MAC code. In a similar way, MAC codes can be used to control which machines on a network can access files and other shared resources. For example, I've set up my wireless link to the Internet so that only two MAC codes can ever gain access to it (restricting access to the network cards built into my two computers). That helps to stop other people in nearby buildings (or in the street) hacking into my connection or using it by mistake.
The bigger you make a network, the more extra parts you need to add to make it function efficiently. Signals can travel only so far down cables or over wireless links so, if you want to make a big network, you have to add in devices called repeaters—effectively signal boosters. You might also need bridges, switches, and routers—devices that help to link together networks (or the parts of networks, which are known as segments), regulate the traffic between them, and forward traffic from one part of a network to another part.
Understanding computer networks with layers
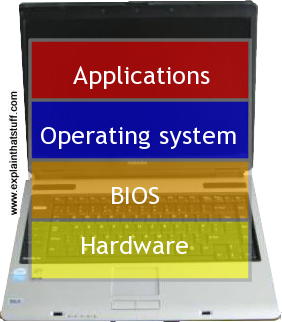
Photo: Computer architecture: We can think of computers in layers, from the hardware and the BIOS at the moment to the operating system and applications at the top. We can think of computer networks in a similar way.
Computers are general-purpose machines that mean different things to different people. Some of us just want to do basic tasks like word processing or chatting to friends on Facebook and we couldn't care less how that happens under the covers—or even that we're using a computer to do it (if we're using a smartphone, we probably don't even think what we're doing is "computing"—or that installing a new app is effectively computer programming). At the opposite end of the spectrum, some of us like modifying our computers to run faster, fitting quicker processors or more memory, or whatever it might be; for geeks, poking around inside computers is an end in itself. Somewhere in between these extremes, there are moderately tech-savvy people who use computers to do everyday jobs with a reasonabe understanding of how their machines work. Because computers mean different things to different people, it can help us to understand them by thinking of a stack of layers: hardware at the bottom, the operating system somewhere on top of that, then applications running at the highest level. You can "engage" with a computer at any of these levels without necessarily thinking about any of the other layers. Nevertheless, each layer is made possible by things happening at lower levels, whether you're aware of that or not. Things that happen at the higher levels could be carried out in many different ways at the lower levels; for example, you can use a web browser like Firefox (an application) on many different operating systems, and you can run various operating systems on a particular laptop, even though the hardware doesn't change at all.
Computer networks are similar: we all have different ideas about them and care more or less about what they're doing and why. If you work in a small office with your computer hooked up to other people's machines and shared printers, probably all you care about is that you can send emails to your colleagues and print out your stuff; you're not bothered how that actually happens. But if you're charged with setting up the network in the first place, you have to consider things like how it's physically linked together, what sort of cables you're using and how long they can be, what the MAC addresses are, and all kinds of other nitty gritty. Again, just like with computers, we can think about a network in terms of its different layers—and there are two popular ways of doing that.
The OSI model
Perhaps the best-known way is with what's called the OSI (Open Systems Interconnect) model, based on an internationally agreed set of standards devised by a committee of computer experts and first published in 1984. It describes a computer network as a stack of seven layers. The lower layers are closest to the computer hardware; the higher levels are closer to human users; and each layer makes possible things that happen at the higher layers:
- Physical: The basic hardware of the network, including cables and connections, and how devices are hooked up into a certain network topology (ring, bus, or whatever). The physical layer isn't concerned in any way with the data the network carries and, as far as most human users of a network are concerned, is uninteresting and irrelevant.
- Data link: This covers things like how data is packaged and how errors are detected and corrected.
- Network: This layer is concerned with how data is addressed and routed from one device to another.
- Transport: This manages the way in which data is efficiently and reliably moved back and forth across the network, ensuring all the bits of a given message are correctly delivered.
- Session: This controls how different devices on the network establish temporary "conversations" (sessions) so they can exchange information.
- Presentation: This effectively translates data produced by user-friendly applications into computer-friendly formats that are sent over the network. For example, it can include things like compression (to reduce the number of bits and bytes that need transmitting), encryption (to keep data secure), or converting data between different character sets (so you can read emoticons ("smileys") or emojis in your emails).
- Application: The top level of the model and the one closest to the user. This covers things like email programs, which use the network in a way that's meaningful to human users and the things they're trying to achieve.
OSI was conceived as a way of making all kinds of different computers and networks talk to one another, which was a major problem back in the 1960s, 1970s, and 1980s, when virtually all computing hardware was proprietary and one manufacturer's equipment seldom worked with anyone else's.
The TCP/IP (DARPA) model
If you've never heard of the OSI model, that's quite probably because a different way of hooking up the world's computers triumphed over it, delivering the amazing computer network you're using right now: the Internet. The Internet is based on a two-part networking system called TCP/IP in which computers hook up over networks (using what's called TCP, Transmission Control Protocol) to exchange information in packets (using the Internet Protocol, IP). We can understand TCP/IP using four slightly simpler layers, sometimes known as the TCP/IP model (or the DARPA model, for the US government's Defense Advanced Research Projects Agency that sponsored its development):
- Network Access (sometimes called the Network Interface layer): This represents the basic network hardware, and corresponds to the Physical and Data link layers of the OSI model. Your Ethernet or Wi-Fi connection to the Internet is an example.
- Internet (sometimes called the Network layer): This is how data is sent over the network and it's equivalent to the Network layer in the OSI model. IP (Internet Protocol) packet switching—delivering actual packets of data to your computer from the Internet—works at this level.
- Transport: This corresponds to the Transport layer in the OSI model. TCP (Transmission Control Protocol) works at this level, administering the delivery of data without actually delivering it. TCP converts transmitted data into packets (and back again when they're received) and ensures those packets are reliably delivered and reassembled in the same order in which they were sent.
- Application: Equivalent to the Session, Presentation, and Application layers in the OSI model. Well-known Internet protocols such as HTTP (the under-the-covers "conversation" between web browsers and web servers), FTP (a way of downloading data from servers and uploading them in the opposite direction), and SMTP (the way your email program sends mails through a server at your ISP) all work at this level.

Artwork: The TCP/IP model is easy to understand. In this example, suppose you're emailing someone over the Internet. Your two devices are, in effect, connected by one long "cable" running between their network cards. That's what the green Network Access layer at the bottom represents. Your email is transmitted as packets (orange squares) using the Internet Protocol (IP), illustrated by the orange Internet layer. Transmission Control Protocol (TCP) oversees this process in the blue Transport layer; and, in effect, TCP and IP work together. At the top, in the Application layer, you sit at your computer using an email program (an application) that uses all the layers below.
While the OSI model is quite an abstract and academic concept, rarely encountered outside books and articles about computer networking, the TCP/IP model is a simpler, easier-to-understand, and more practical proposition: it's the bedrock of the Internet—and the very technology you're using to read these words now.
As we saw above, higher levels of the basic computing models are independent of the lower levels: you can run your Firefox browser on different Windows operating systems or Linux, for example. The same applies to networking models. So you can run many applications using Internet packet switching, from the World Wide Web and email to Skype (VoIP) and Internet TV. And you can hook your computer to the net using WiFi or wired broadband or dialup over a telephone line (different forms of network access). In other words, the higher levels of the model are doing the same jobs even though the lower levels are working differently.
I have quite the day tomorrow and you can take it from here >









